What is security awareness training?
Security awareness training is a formal process for educating employees about computer security and the best practices for maintaining a safe and secure working environment. This type of training typically includes strategies for managing passwords, understanding the tactics that hackers might use, such as phishing, and the protocols for reporting security breaches. The aim is to create a company-wide awareness of security threats and to empower employees to recognize and prevent security incidents before they occur.
Why is security awareness training important?
Security awareness training is important because it:
- Reduces Risk of Breaches: Educates employees on recognizing and avoiding cyber threats, significantly reducing the risk of security breaches.
- Compliance with Regulations: Helps organizations comply with legal and regulatory requirements for data protection and privacy.
- Protects Organizational Assets: Helps safeguard the company’s sensitive data and intellectual property by ensuring that employees are aware of security best practices.
- Builds a Security Culture: Fosters a culture of security within the organization where everyone understands their role in maintaining security.
- Minimizes Damage: In the event of a security incident, a well-trained workforce can react swiftly, potentially minimizing the damage caused.
- Cost-Efficiency: Prevents financial losses associated with data breaches, including fines, lost business, and damage to the organization’s reputation.
- Customer Trust: Enhances customer confidence and trust in the business’s ability to protect their personal information.
- Empowers Employees: Provides employees with the knowledge and confidence to handle security threats, making them an active part of the solution.
Why do your employees need security awareness training?
Employees need security awareness training for several critical reasons:
- Human Error Reduction: It helps to minimize the risk of security incidents caused by employee oversight or mistakes.
- Threat Awareness: Empowers employees to recognize and respond to security threats, such as phishing, malware, and social engineering attacks.
- Data Protection: Educates staff on handling sensitive information correctly, crucial for maintaining confidentiality and integrity.
- Regulatory Compliance: Ensures that employees are aware of and can adhere to industry regulations and standards, helping to avoid legal penalties.
- Response to Incidents: Trains employees on the proper actions to take when they suspect a security breach, ensuring quick and effective response.
- Cultural Change: Builds a strong security culture where security becomes a daily operational habit, not just a checklist item.
- Maintain Reputation: Helps protect the company’s reputation by preventing breaches that can lead to negative publicity.
- Cybersecurity Reinforcement: Acts as a continuous reminder that security is everyone’s responsibility, reinforcing best practices across the organization.
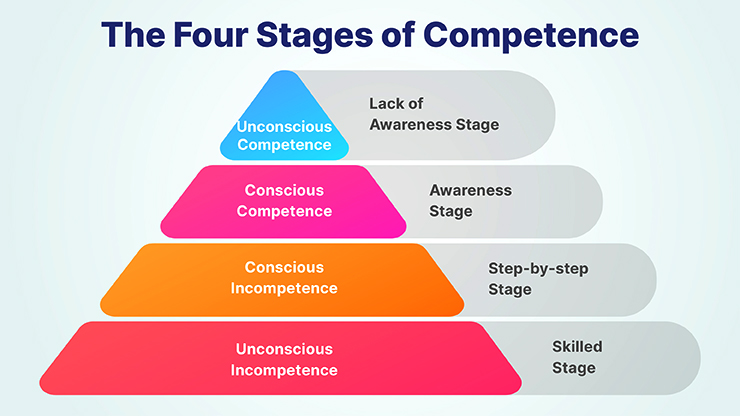
What is the difference between security awareness and security training?
Security awareness and security training are related concepts but serve different purposes within an organization’s overall security strategy.
Security Awareness is about creating a general understanding among employees about the importance of security. It’s designed to be an ongoing process to keep security at the forefront of everyone’s mind. Awareness initiatives do not typically provide detailed instructions on how to execute security protocols but instead aim to alter behavior and cultivate a security-conscious culture. They make employees aware of security policies, the importance of their role in maintaining security, and the potential threats that can affect the organization.
Security Training, on the other hand, is more structured and formal. It involves teaching employees specific skills and procedures necessary to protect the organization’s information assets. Security training is often role-specific and provides detailed instructions on how to perform certain tasks, such as managing passwords, encrypting data, or responding to a security incident. The focus is on developing the knowledge and skills needed to perform tasks securely.
What should a strong security awareness training include?
A strong security awareness training program should include the following elements:
- Comprehensive Curriculum: Covering a range of topics such as phishing, malware, password security, social engineering, mobile device security, and physical security.
- Regulatory Compliance: Information on relevant laws, regulations, and standards such as GDPR, HIPAA, or PCI-DSS, explaining how compliance affects daily tasks.
- Risk Management: Education on the potential risks associated with security lapses and the impact they can have on the organization.
- Incident Reporting: Clear instructions on how to report security incidents quickly and efficiently.
- Practical Examples: Real-life case studies or examples that illustrate the consequences of security breaches.
- Interactive Content: Engaging materials like quizzes, games, and simulations that encourage active participation.
- Behavioral Change Strategy: A focus on changing behaviors, not just imparting knowledge, including how to cultivate good cybersecurity habits.
- Continuous Learning: Regular updates and refreshers on the training content to keep up with new threats and reinforce the principles.
- Testing and Metrics: Tests to measure employee understanding and retention of security concepts, with metrics to track the program’s effectiveness.
- User-Specific Content: Role-based training that is relevant to the specific security concerns of different departments or job functions.
- Response Procedures: Training on the organization’s specific security policies and procedures, including response plans for different types of incidents.
- Resources for Further Learning: Additional resources for employees who want to learn more about specific security topics.
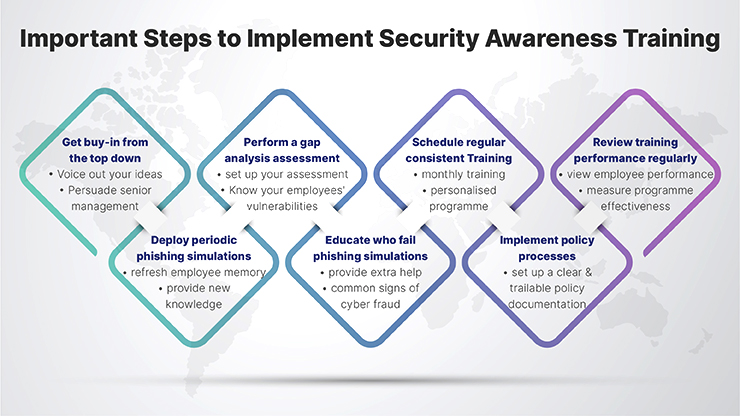
How to create and implement a successful security awareness training program
Creating and implementing a successful security awareness training program involves several steps:
- Assess Needs and Risks:
- Identify the specific security risks relevant to your organization.
- Understand the current level of security awareness among employees.
- Define Objectives:
- Determine what you want the program to achieve, e.g., compliance with specific regulations, behavior change, or knowledge improvement.
- Set clear, measurable goals
- Develop the Content:
- Create engaging and relevant content tailored to different roles within the organization.
- Ensure content is up-to-date with the latest security threats and practices.
- Choose the Right Tools and Methods:
- Decide on the delivery method (e.g., e-learning, instructor-led training, webinars, interactive workshops).
- Consider using gamification or simulations for more engagement.
- Plan the Implementation:
- Develop a rollout plan that includes a schedule and format (e.g., all at once, in stages, ongoing).
- Determine how to integrate the training into new hire onboarding processes.
- Communicate the Program:
- Inform employees about the importance of the program and its benefits.
- Clearly communicate the expectations and the schedule.
- Execute the Training:
- Launch the program according to the plan.
- Encourage management to participate and endorse the training to emphasize its importance.
- Measure Effectiveness:
- Use quizzes, surveys, and other methods to assess employee understanding and retention.
- Monitor for a reduction in security incidents or improvements in compliance.
- Gather Feedback:
- Ask for employee feedback to identify areas of improvement.
- Make adjustments based on the feedback received.
- Update Regularly:
- Keep the program content current with evolving security threats.
- Regularly review and update the training materials.
- Reinforce and Remind:
- Provide regular updates, tips, and reminders to keep security top of mind.
- Use newsletters, posters, or emails to reinforce key messages.
- Create a Security Culture:
- Encourage a culture where security is everyone’s responsibility.
- Recognize and reward employees who contribute positively to security.
How to promote a work culture that prioritizes security awareness
Promoting a work culture that prioritizes security awareness involves strategic efforts across all levels of the organization. Here’s how you can do it:
- Leadership Endorsement: Have leaders advocate for security awareness, demonstrating its importance through their actions and communications.
- Integrate Security into Core Values: Embed security awareness into the organizational values and mission statement to signal its role in the company’s success
- Regular Communication: Use internal communications to regularly discuss the importance of security, share updates, and celebrate successes.
- Engaging Training: Offer engaging, interactive security awareness training that is relevant and personalized to different roles.
- Gamification: Introduce elements of competition and reward, such as leaderboards or recognition for security-conscious behavior.
- Employee Empowerment: Empower employees to take personal responsibility for security by providing the tools and support they need to identify and report threats.
- Clear Policies and Procedures: Develop clear, accessible policies and procedures for data security and ensure they are widely communicated and easy to follow.
- Security Champions: Appoint security champions within different departments to advocate for security practices and act as go-to experts.
- Feedback and Improvement: Encourage and act on employee feedback regarding security practices to improve the program continuously.
- Incentives and Rewards: Offer incentives for proactive security behaviors or for completing training milestones.
- Real-life Examples: Share stories and case studies that illustrate the real-world impact of security awareness.
- Response Plan Familiarity: Ensure that all employees are familiar with the incident response plan and understand their role in it.
- Visibility of Security Measures: Make security measures visible within the organization to remind employees of their presence and importance.
- Regular Audits and Assessments: Conduct regular security audits and assessments, and share the results and improvement plans with the workforce
How often should security awareness training occur?
Security awareness training should occur regularly to be effective. The frequency can depend on various factors, including the organization’s size, the sensitivity of the information handled, compliance requirements, and the evolving threat landscape. However, a recommended best practice is as follows:
- Annual Training: At a minimum, conduct formal security awareness training annually to ensure all employees are up-to-date with the organization’s policies and the latest security practices.
- Ongoing Education: Supplement annual training with ongoing education throughout the year. This could include monthly newsletters, regular security tips, or updates on the latest threats.
- Role-Specific Training: Provide additional training when employees are given new security responsibilities or when there are changes in security procedures.
- New Hire Training: Ensure that new employees receive security awareness training as part of their onboarding process.
- After Security Incidents: Provide additional targeted training after any security incident to address any emerging threats or vulnerabilities that have been identified.
- When Compliance Requires: Some regulations may dictate more frequent training. Always adhere to these requirements.
What is the purpose of security awareness training policy?
The purpose of a security awareness training policy is to:
- Establish Expectations: Clearly define what is expected of employees regarding security awareness within the organization.
- Standardized Training: Ensure that all employees receive consistent information and instruction on how to handle and protect sensitive information and assets.
- Promote a Security Culture: Help create a culture of security within the organization where every employee understands the importance of their role in maintaining security.
- Compliance with Regulations: Assist in meeting legal and regulatory requirements for employee training on data protection and privacy.
- Mitigate Risks: Reduce the risk of data breaches and other security incidents by ensuring employees are aware of potential threats and how to avoid them.
- Responsiveness: Prepare employees to respond appropriately to security incidents, should they occur.
- Continuous Improvement: Provide a framework for ongoing evaluation and improvement of the security awareness program to adapt to new threats and changes in the business environment.
- Accountability: Set the groundwork for accountability by outlining consequences for non-compliance with the organization’s security policies and procedures.
FAQ
- Why is user security awareness important?
Personal Data Protection: Users, often the first line of defense, need to be aware of how to protect their personal data from cyber threats.
Preventing Identity Theft: Awareness helps in recognizing and avoiding potential threats that can lead to identity theft.
Safe Online Behavior: Educating users on safe online practices prevents risky behaviors that can compromise their security.
Empowerment and Responsibility: Knowledgeable users are more empowered to make safer choices online and take responsibility for their digital footprint. - Why is information security and its awareness important?
Protection of Sensitive Data: Information security awareness is crucial for protecting sensitive personal and business data from unauthorized access and breaches.
Compliance with Regulations: Awareness ensures adherence to various data protection laws and regulations, avoiding legal consequences.
Maintaining Trust: Businesses that prioritize information security maintain and build trust with their clients and partners.
Minimizing Risks: Awareness of information security reduces the risk of data breaches and cyber-attacks, thereby protecting the organization’s assets and reputation. - What is the importance of user security?
Individual Safety: Ensures the safety and privacy of individuals in the digital space.
Preventing Unauthorized Access: By securing user accounts and data, unauthorized access and potential damages are minimized.
Enabling Secure Transactions: In the context of online banking and shopping, user security is vital for safe and secure transactions.
Building Digital Trust: Secure users contribute to a safer digital environment, fostering trust in online systems and interactions. - How important is cyber security awareness?
Mitigating Cyber Threats: Awareness of cyber security helps individuals and organizations recognize and respond to various cyber threats effectively.
Adapting to Evolving Threats: As cyber threats evolve, staying aware and educated is crucial for adapting to new risks.
Cultivating a Secure Culture: In organizations, cyber security awareness fosters a culture where everyone contributes to the overall security posture.
Economic Implications: It helps avoid the potentially severe financial repercussions associated with data breaches and cyber-attacks.