The Health Insurance Portability and Accountability Act (HIPAA) is a U.S. legislation designed to safeguard the privacy and security of patients’ health information. A HIPAA breach occurs when there’s an unauthorized access, use, disclosure, or acquisition of protected health information (PHI) in a manner not permitted under the Privacy Rule. Such breaches can result from various incidents, ranging from lost or stolen electronic devices containing PHI to hacking or cyberattacks on health networks. Organizations subject to HIPAA are required to have preventive measures in place and to notify affected individuals and the Department of Health & Human Services in case of breaches. The implications of a breach can be severe, including penalties, legal actions, and reputational damages.
What is the HIPAA Breach Notification rule?
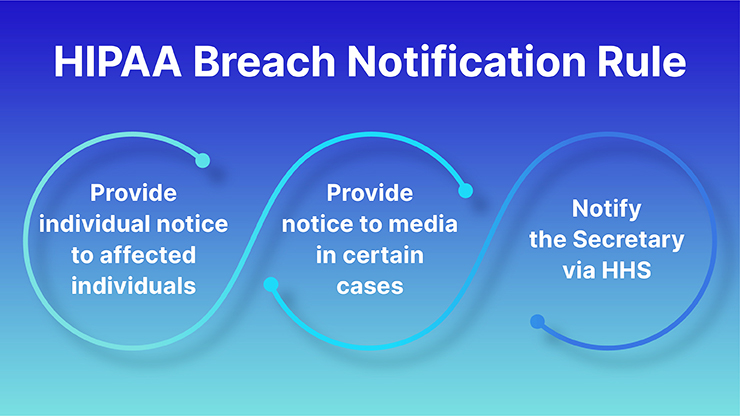
The Health Insurance Portability and Accountability Act (HIPAA) Breach Notification Rule is a U.S. regulation that mandates covered entities and their business associates to provide notification to affected individuals, the U.S. Department of Health and Human Services (HHS), and, in certain cases, the media, following a breach of unsecured protected health information (PHI).
Here are the key components of the Breach Notification Rule:
- Definition of a Breach: A breach is, generally, an impermissible use or disclosure under the Privacy Rule that compromises the security or privacy of the protected health information. An impermissible use or disclosure of protected health information is presumed to be a breach unless the covered entity or business associate demonstrates that there is a low probability that the protected health information has been compromised.
- Risk Assessment: If there’s an impermissible use or disclosure of PHI, covered entities and business associates must perform a risk assessment to determine the probability that the PHI has been compromised. This assessment considers at least the following factors:
- The nature and extent of the PHI involved.
- The unauthorized person who used the PHI or to whom the disclosure was made.
- Whether the PHI was actually acquired or viewed.
- The extent to which the risk to the PHI has been mitigated.
- Notifications:
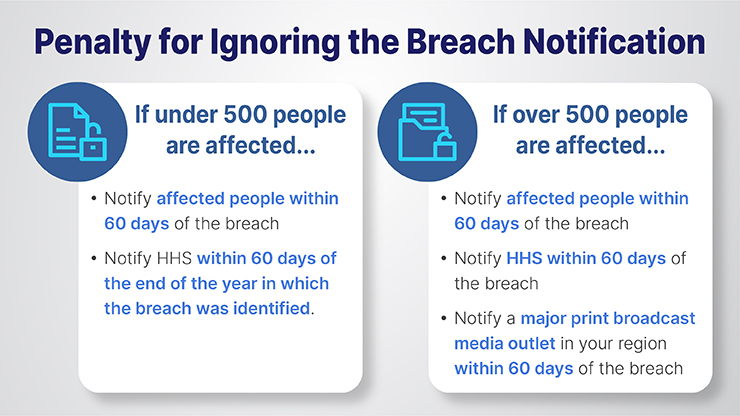
- Affected Individuals: Must be notified without unreasonable delay and no later than 60 days following the discovery of a breach.
- HHS: Breaches affecting 500 or more individuals must be reported to HHS without unreasonable delay and no later than 60 days after discovery. Breaches affecting fewer than 500 individuals must be reported to HHS annually.
- Media: For breaches affecting 500 or more individuals in a state or jurisdiction, media outlets serving the state or jurisdiction must also be notified no later than 60 days after discovery.
- Content of the Notification: The notice to affected individuals must include:
- A brief description of the breach, including the date of the breach and the date of discovery.
- The types of PHI involved in the breach.
- Steps individuals should take to protect themselves from potential harm.
- A description of what the covered entity is doing to investigate the breach, mitigate the harm, and prevent future breaches.
- Contact information for individuals to ask questions or learn additional information.
- Methods of Notification: This includes written notification, either by postal mail or email (if the affected individual has agreed to email communication), and a toll-free phone number for affected individuals to ask questions or learn additional information.
- Breach Log: Covered entities must maintain a log or other documentation of breaches, even those affecting fewer than 500 individuals.
- Business Associates: If the breach occurs at or by a business associate, that entity must notify the covered entity without unreasonable delay and no later than 60 days after the discovery of the breach.
Why should organizations follow the HIPAA Breach Notification rule?
Organizations should adhere to the HIPAA Breach Notification Rule for several important reasons:
Legal Obligations: First and foremost, the rule is a federal requirement. Non-compliance can lead to significant legal repercussions.
Financial Penalties: Failure to comply with the rule can result in substantial fines. These fines vary based on the level of perceived negligence and can range from $100 to $50,000 or more per violation, with a maximum annual penalty of $1.5 million for identical violations.
Reputation Management: Trust is essential in the healthcare sector. If patients and clients feel their personal and medical information isn’t safe with an organization, they might choose to seek care or services elsewhere. Notifying affected parties of breaches as required helps in maintaining some level of trust, and showing transparency and responsibility.
Patient Protection: The rule is designed to protect patients. When individuals are informed of breaches, they can take actions to safeguard their identities and health information, such as by monitoring their accounts or seeking identity protection services.
Operational Integrity: The process of investigating and responding to a breach often identifies vulnerabilities in an organization’s systems or processes. Addressing these issues not only ensures compliance but also strengthens the organization’s overall data security framework.
Mitigation of Further Harm: When affected individuals are notified promptly, they can take preventive measures against potential identity theft or fraud that could result from the breach.
Maintaining Stakeholder Relations: This includes not only patients but also business associates, partners, and investors. Adhering to federal regulations and ensuring prompt notifications can foster a sense of reliability and professionalism.
Insurance and Liability Considerations: Some insurance policies may have stipulations about compliance with federal laws, including HIPAA. Reporting and addressing breaches as required can be crucial for insurance claims and can potentially reduce liability in the event of lawsuits.
Moral Responsibility: Beyond financial and legal reasons, healthcare entities have a moral and ethical responsibility to protect patient data. By following the Breach Notification Rule, organizations are upholding their duty to prioritize patient well-being and privacy.
What is a breach?
In a general context, a “breach” refers to an incident where rules, laws, security, or standards are broken or violated. Depending on the context in which it’s used, the term can have various meanings. Here are some interpretations:
Security Breach: This usually refers to an incident where unauthorized access is gained to a secure or protected system, often with the intent of stealing, viewing, or corrupting data. Examples include hacking into a computer network or unauthorized access to a database.
Data Breach: This is a subset of a security breach where sensitive, protected, or confidential data is copied, transmitted, viewed, or stolen by an unauthorized individual. Examples include the unauthorized acquisition of personal information, credit card data, or health records.
Contractual Breach: In legal terms, a breach can refer to a violation of the terms of a contract. For instance, if one party fails to deliver on its commitments outlined in a contract, they have breached that contract.
Breach of Trust: This refers to a situation where someone violates the trust or responsibility placed on them, either in a personal or professional setting.
Breach of Law: This is when an individual or entity violates a provision of the law or legal obligation.
Physical Breach: This can refer to a situation where a physical barrier or security measure, like a wall or a security checkpoint, is bypassed or broken.
HIPAA Breach Notification Rule Requirements
The HIPAA (Health Insurance Portability and Accountability Act) Breach Notification Rule outlines the steps that covered entities and their business associates must take when there’s a breach of unsecured protected health information (PHI). Here are the main requirements of the rule:
- Definition of a Breach: A breach is generally an impermissible use or disclosure under the Privacy Rule that compromises the security or privacy of the PHI. Unless it’s demonstrated that there’s a low probability that the PHI has been compromised, an impermissible use or disclosure is presumed to be a breach.
- Risk Assessment: If an impermissible use or disclosure of PHI occurs, a risk assessment should be conducted to determine if it constitutes a breach. This assessment often considers:
- The nature and extent of the PHI involved.
- The unauthorized person who used the PHI or to whom the disclosure was made.
- Whether the PHI was actually acquired or viewed.
- The extent to which the risk to the PHI has been mitigated.
- Notification to Affected Individuals: If a breach is determined:
- Affected individuals must be notified without unreasonable delay and no later than 60 days following the discovery of the breach.
- The notification should include a description of the breach, the types of information involved, steps individuals should take to protect themselves, what the covered entity is doing to investigate and mitigate the breach, and contact information for further questions.
- Notification to the U.S. Department of Health and Human Services (HHS):
- Breaches affecting 500 or more individuals must be reported to HHS without unreasonable delay and no later than 60 days after discovery.
- Breaches affecting fewer than 500 individuals must be reported to HHS annually.
- Notification to the Media: For breaches affecting 500 or more individuals in a specific state or jurisdiction, media outlets serving that state or jurisdiction must also be notified without unreasonable delay and no later than 60 days after discovery.
- Content of the Notification: Notifications should provide:
-
- A brief description of what happened, including the date of the breach and its discovery.
- The types of PHI involved.
- Steps individuals should take in response.
- A description of the covered entity’s actions regarding the breach.
- Contact information for further details.
- Breach Log: All breaches, including those affecting fewer than 500 individuals, should be documented in a breach log or similar documentation.
- Business Associates: If a breach occurs at or by a business associate, they must notify the covered entity of the breach without unreasonable delay and no later than 60 days from its discovery.[Also Read: Understanding HIPAA Privacy Rule: The Three Fundamental Rules to Keep in Mind]
What is the penalty for ignoring the Breach Notification requirement?
penalties for non-compliance with the HIPAA Breach Notification Rule can be substantial, both in terms of financial costs and reputational damage. The U.S. Department of Health and Human Services’ Office for Civil Rights (OCR) enforces these regulations.
Here’s a breakdown of the potential penalties:
- Tiered Civil Penalties:
Tier 1: The covered entity or business associate did not know (and by exercising reasonable diligence would not have known) that it violated the provision. The penalty ranges from $100 to $50,000 per violation, with an annual maximum of $25,000 for repeated violations.
Tier 2: The violation was due to reasonable cause, but not willful neglect. Penalties range from $1,000 to $50,000 per violation, with an annual maximum of $100,000 for repeated violations.
Tier 3: The violation was due to willful neglect but was corrected in a timely manner (typically within 30 days). Penalties range from $10,000 to $50,000 per violation, with an annual maximum of $250,000 for repeated violations.
Tier 4: The violation was due to willful neglect and was not corrected in a timely manner. Penalties are $50,000 per violation, with an annual maximum of $1.5 million.
- Criminal Penalties: In addition to civil penalties, criminal charges can be brought against entities that knowingly and improperly disclose PHI or otherwise violate HIPAA. These penalties can range from fines to imprisonment, depending on the severity and intent of the violation.
- Unknowingly or with reasonable cause: Fine up to $50,000 and/or imprisonment up to 1 year.
- Under false pretenses: Fine up to $100,000 and/or imprisonment up to 5 years.
- With intent to sell, transfer, or use for personal gain, commercial advantage, or malicious harm: Fine up to $250,000 and/or imprisonment up to 10 years.
- Other Consequences: Beyond monetary fines and potential imprisonment:
- Reputational Damage: News of a breach and the subsequent failure to notify affected individuals can severely harm an organization’s reputation.
- Increased Scrutiny: Entities found in violation may be subject to more frequent and rigorous audits by the OCR.
- Loss of Business: Trust is crucial in healthcare. Entities that fail to comply with regulations may find patients and partners choosing to work with more compliant and trustworthy entitie
FAQ
1. What is a HIPAA breach notification letter?
A HIPAA breach notification letter is a formal communication sent by a covered entity or business associate to individuals whose protected health information (PHI) has been compromised in a breach. This letter informs the affected parties of the breach, describes the type and extent of the compromised data, provides guidance on steps they can take to protect themselves, and often outlines what the organization is doing in response to the breach. When should an individual be notified about the breach of PHI?
2. What are the rules for breach notification?
According to the HIPAA Breach Notification Rule, affected individuals should be notified without unreasonable delay, but no later than 60 days from the discovery of the breach.
3. What are the four criteria for determining a breach?
When assessing whether an impermissible use or disclosure of PHI constitutes a breach, entities should consider the following four factors:
Nature and Extent of PHI: This includes the type of PHI and the likelihood of re-identification. For instance, was it a patient’s name and address, or more sensitive information like a medical history or social security number?
Unauthorized Person Involved: To whom was the data disclosed or who accessed the data without authorization? Was it another healthcare provider, or was it someone outside the healthcare system?
Whether PHI was Actually Acquired or Viewed: Was the data merely exposed, or was it actually accessed and viewed?
The extent to Which Risk Has Been Mitigated: Has the risk to the PHI been lowered, for instance, through retrieval of the data or assurances that the data won’t be further used or disclosed?
4. What are the rules for breach notification?
Affected Individuals: Must be notified without unreasonable delay and no later than 60 days following the discovery of a breach.
Notification to the U.S. Department of Health and Human Services (HHS): Breaches affecting 500 or more individuals must be reported to HHS without unreasonable delay and no later than 60 days after discovery. Breaches affecting fewer than 500 individuals must be reported to HHS annually.
Media Notification: Breaches affecting 500 or more individuals in a specific state or jurisdiction require notification to media outlets serving that area, again no later than 60 days after discovery.
Content of Notification: The notice should include details about the breach, types of data involved, steps affected individuals should take, actions the organization is taking in response, and contact information for further inquiries.
Method of Notification: Typically, individuals are notified via first-class mail. If the affected individual has agreed to electronic communication, then email may be used. If contact information for 10 or more individuals is out-of-date, a substitute form of notice, such as a public posting or media announcement, may be required.