Neglecting the three HIPAA rules can lead to large fines, loss of face, and for an employee worker – loss of job. Businesses can lose up to 1.5 million dollars as fines. So, if you are covered under HIPAA, you must comply with the three HIPAA rules.
Why the 3 rules of HIPAA are necessary
When discussing HIPAA, you may often come across references to three critical rules: the Privacy Rule, the Security Rule, and the Breach Notification Rule.
Why are these rules so significant? Non-compliance can lead to large civil monetary fines, reaching up to $1.5 million, or even criminal sanctions. Furthermore, breaches can tarnish your organization’s reputation. Hence, if your enterprise falls under the category of a covered entity as per HIPAA, adhering to these three rules is paramount.
To ensure clarity, let’s dive deeper into the specifics of each rule and the necessary measures for compliance.
Who needs to comply with the 3 HIPAA rules?
Every entity dealing with Protected Health Information (PHI) is required to comply with these rules. This includes Healthcare providers, from large hospitals to private practices. Health insurance companies and clearinghouses. Business associates of the above entities can range from billing companies to software providers.
Even if an entity doesn’t directly deal with patients, but they handle, transmit, or store PHI in any manner, they are bound by HIPAA’s regulations.
The three HIPAA rules
The Health Insurance Portability and Accountability Act (HIPAA) lays out three rules for protecting patient health information.
- The Privacy Rule
- The Security Rule
- The Breach Notification Rule
These three rules set national standards for the purpose. These standards address the issue of protecting health information, which could be used for identifying a person.
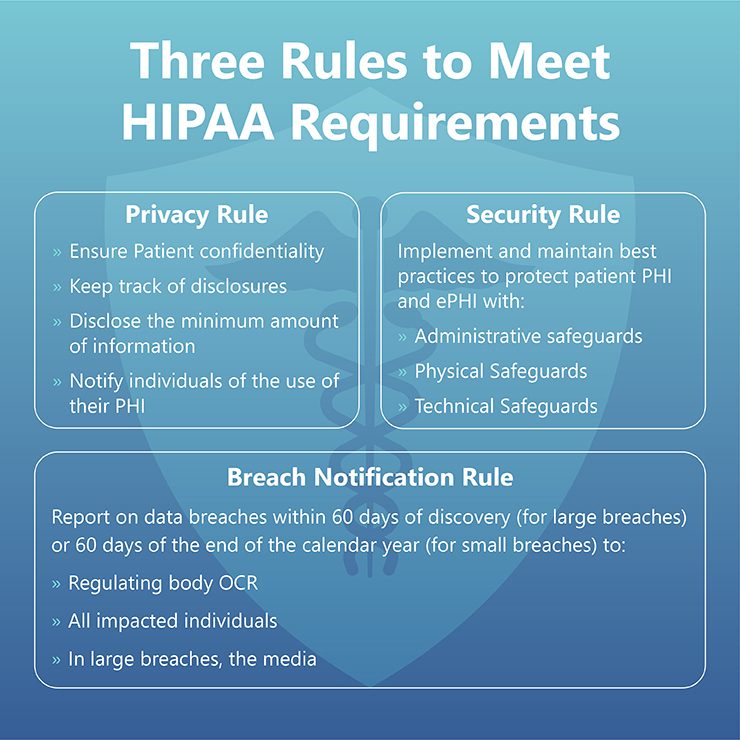
1. The Privacy Rule
The standards set by the Privacy rule address subjects such as:
- Which organizations must follow the HIPAA standards
- What is protected health information (PHI)
- How organizations can share and use PHI
- Permitted usage and disclosure of PHI
- Patient’s rights over their health information
Healthcare entities covered by HIPAA include:
- Health plans
- Health care clearinghouses
- Health care providers
HIPAA also applies to business associates who conduct healthcare transactions for covered entities.
Usage and disclosure limitations
The privacy rule restricts the usage of health information which could identify a person (PHI). Covered entities cannot use or disclose PHI unless:
- It’s permitted under the Privacy rule, or
- The individual has authorized it in writing.
The Privacy rule does not restrict de-identified health information.
2. The Security Rule
The security rule sets the standards for the protection of PHI in electronic format (ePHI).
The Security rule standards cover:
- Which organizations must follow the security rule
- What health information is protected under the security rule
- What safeguards must be in place for the purpose
The security rule covers all healthcare providers who use ePHI. It also covers business associates of such providers.
All the covered entities must protect all ePHI that they create, receive, store, or send. They must:
- Ensure the confidentiality, integrity, and availability of the PHI
- Protect the ePHI against all threats to its security and integrity
- Protect it against impermissible use or disclosure
- Train employees, and ensure compliance with the security rule
- Adapt suitable policies and procedures
The covered entities are also required to perform risk analysis and create a risk management plan to mitigate the risk to ePHI.
The risk analysis process should at least include the following steps.
- Identify potential risks to patient health information
- Create a risk management plan
- Put in place administrative, physical, and technical safeguards
- Conduct HIPAA training, and train workers to follow HIPAA policies and procedures
- Document their risk analysis process
- Conduct risk analysis yearly to identify and mitigate new risks
3. The breach notification rule
HIPAA considers all PHI usage or disclosures that aren’t permitted under the Privacy rule as a breach.
The breach notification rule requires covered entities to send alerts upon discovery of a breach. Once a covered entity becomes aware of a breach, the alerts have to be sent within next 60 days.
Covered entities are required to alert:
- Affected individuals
- Health and Human Services (HHS)
- Media, if necessary
Business associates of a covered entity need to alert their covered entity too.
If the breach affects more than 500 people, the HHS must be notified immediately. The HHS would post it on their website. The covered entity would also need to post the message on their website.
Organizations may also choose not to send alerts, but only if they can prove that there is a low probability of the PHI being compromised.
[Also Read: Understanding HIPAA – Comprehensive Guide to HIPAA Compliance]
Breaking Down the Breach Notification Rule
This rule is particularly pertinent in the event of a data breach. Entities are obligated to:
- Individual notice: Should a breach occur, affected individuals must be notified without undue delay, and in any case, no later than 60 days following the discovery of the breach. This notice should ideally be provided in writing and must contain details about the breach, the type of information compromised, steps individuals should take, and contact information for questions.
- Media notice: For breaches affecting more than 500 residents of a state or jurisdiction, entities are required to notify prominent media outlets in that region. This serves to inform and protect a large group of affected individuals who might not get the notification directly.
- Notice to the Secretary: Lastly, entities must inform the Secretary of Health & Human Services about the breach. If the breach affects more than 500 individuals, this notification must be immediate. For breaches affecting fewer people, entities can maintain a log and submit it annually.
Reportable Breaches and Exceptions
Organizations should consider all impermissible uses and disclosures as a breach of PHI. But, they need to send alerts only for unsecured PHI. Besides this, the breach notification rule is flexible under three more circumstances.
- If it was unintentional or done in good faith, and was within the scope of the authority.
- If it was done unintentionally between two people permitted to access the PHI.
- The organization has a good faith belief that the person to whom the disclosure was made would not be able to retain the PHI.
In any case, the organization should ensure that such incidents don’t reoccur.
Breach alerts are required only for unsecured PHI. If you secured it as specified by this guidance, then you don’t need to send the alerts.
The HHS Office for Civil Rights enforces the three HIPAA rules. Violations of the HIPAA rules may result in fines and penalties. In some cases, criminal penalties may also apply.