As the pandemic relief and stimulus checks begin to head out, the threat of phishing attacks targeting Social Security beneficiaries is deemed to rise. This is because a similar spike was observed last year, in April. Back then, the attacks had increased by 600% when government agencies began distributing funds.
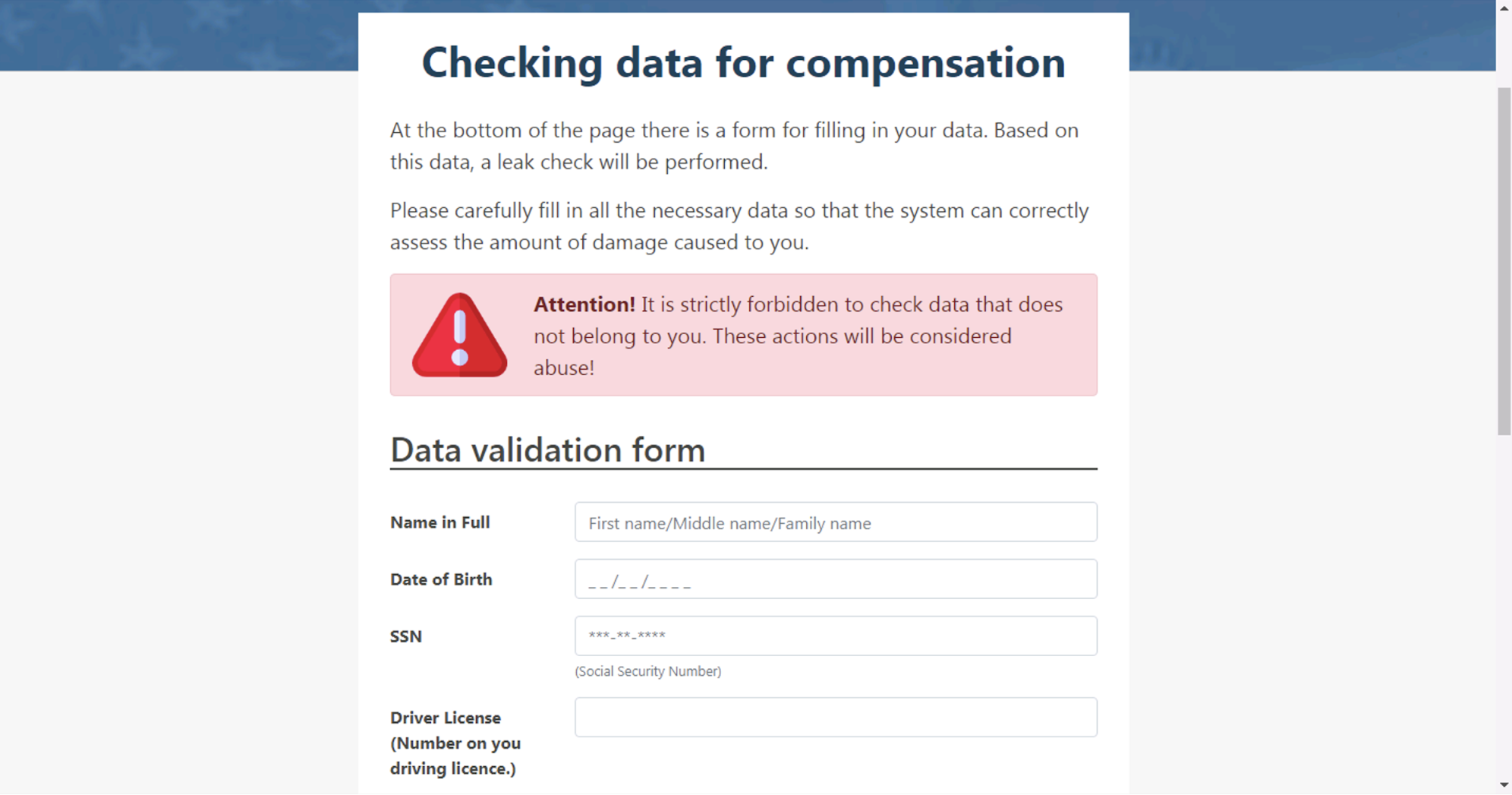
For instance, one of the phishing operations shut down last year, imitated the Federal Trade Commission’s website, and promised $5,800 in relief funds. The phishing website claimed to be a branch of the US Federal trade commission, and tricked people into revealing their social security numbers, date of birth, and driver’s license for identity verification.
A similar spike has been observed in Phishing attacks that are using COVID-19 vaccination as a lure. Such attacks rose by 530% between December and February, this year.
Unfortunately, these attacks aren’t just targeting individuals for personal information. The criminals are targeting office workers as well. Thus, both, individuals and businesses need to comprehend the threat of pandemic-themed phishing attacks, and prepare for them.
You need to understand how such phishing attacks work, how to spot them, and how to report them to the authorities.
In this blog, we’ll take a closer look at the issue of pandemic-themed phishing attacks, and what you can do to protect yourself from them.
How Phishing attacks are exploiting the pandemic to target your business
The trend of COVID-19 themed phishing attacks
First, let us look at the intelligence shared by the threat intelligence team, Unit 42. During the last one year, they have observed about 70,000 phishing pages and emails that used COVID-19 as a bait.
Here’s a list of phishing lures that you should be careful about. You need to exercise caution, when visiting similar pages and clicking on links that lead to such pages.
- Pages disguised as pharmaceutical drug companies, and offering
- Meeting links disguised as links from online meeting platforms, such as Zoom and Microsoft Teams
- Employee forms requesting information for COVID-19 screening
- Websites and emails marketing personal protective gear, such as face masks
- Online offers of free testing kits
- Emails offering assistance with stimulus and relief payment
- Pages disguised as government agencies, offering financial aid
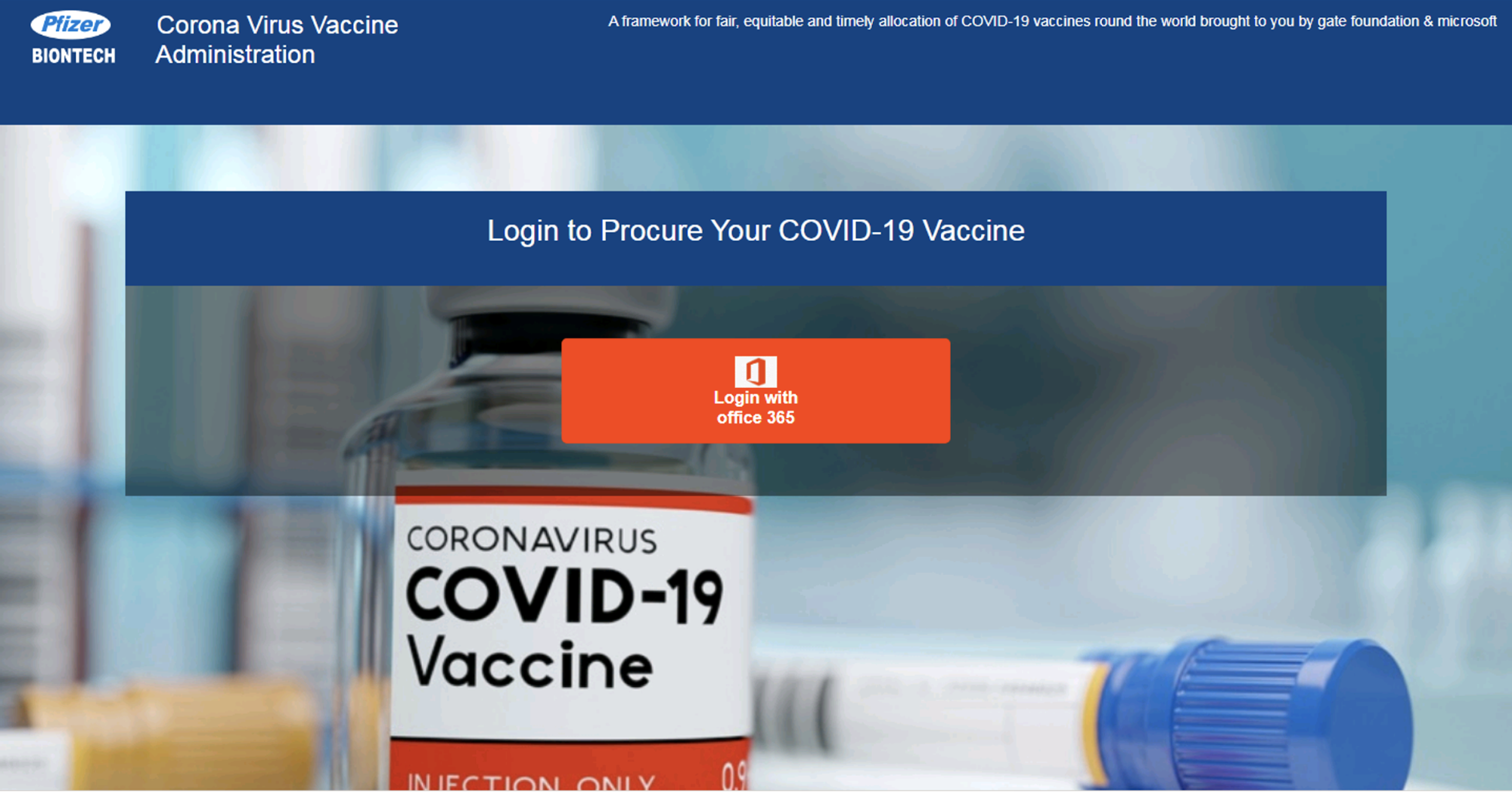
- Vaccine-related pages, including vaccine registration and vaccine purchase
Using these lures, criminals would try to trick you into:
- Exposing your personal information, such as phone number, email, date of birth, social security number or your driver’s license
- Sharing your credentials, such as your Apple ID, Microsoft credentials, VPN login ID and password, and so on
- Downloading a malware on your computer
For this purpose, the criminals use fake pages that duplicate original websites, but need your personal details to proceed. In addition, they also use spoofed emails which seem to come from people you are acquainted with. The intent of such emails is to trick you into
- Opening a malicious attachment, which would install a malware on your computer
- Clicking a link that would initiate a malware download, or else it would redirect you to a phishing page, where you’d need to enter your credentials.
Troublingly, these attacks are slated to rise in the next few months. Especially those that use vaccines and the stimulus program as baits.
[Also Read: Email Phishing and Security: A Detailed Overview of Types and Techniques]
How are phishing attacks carried out?
In most cases, you’d receive spoofed emails from a company executive, asking you to login using your office credentials. Or, you’d receive an email offering to assist you with the stimulus program. Similarly, you may receive emails that would trick you into opening a malicious attachment.
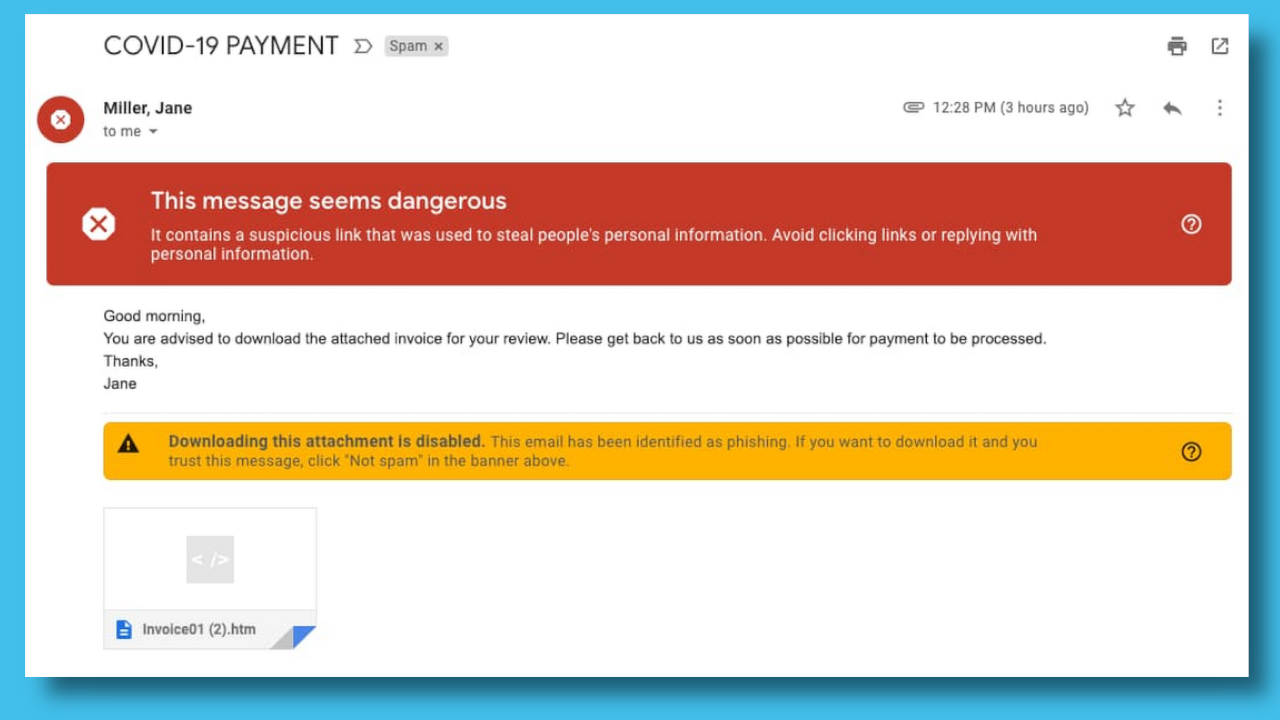
Fortunately, most email services offer protection from phishing. For example, Google claims that their email service blocks phishing emails automatically. In addition, suspicious emails that manage to bypass their filters display warning messages to alert the receiver of the email.
You should treat such messages with caution. If the message is from a vendor, cross check it with your vendor. If the message is from your CEO, discuss it with your manager.
In addition, check the links, email addresses, and the content of the email very carefully. Inspect the email for grammatical errors, spoofed email addresses, the link and the attachment as well.
As a rule of thumb, never open an attachment that you weren’t expecting. As a precaution, check with the sender if they sent the email to you.
Next, hover over the link and see if there’s anything suspicious about it. In our opinion, never click an email link. You should copy and paste it in a new window.
Similarly, before entering sensitive information on a page, check the website address in the address bar. This way, you can ascertain if you are not on a phishing page. This is because criminals create phishing pages by spoofing the original web addresses. But be careful, even if the website name is correct, the page could be a phishing lure. This is because, in certain instances, criminals have hacked the original website, and added a malicious page to it. So, you need to look at the entire URL to ascertain if the page is genuine.
In Conclusion
Lastly, a word of caution about the effectiveness of phishing detectors. In certain cases, like the email below, criminals bypassed the protection by hiding the lure behind a login button.
To put it another way, due diligence is important for safeguarding your business and personal data. This is because emails are inherently an insecure mode of communication. They can be intercepted and manipulated by a cybercriminal by compromising the computers of the sender, receiver, or the email service provider. So, we advise our customers to avoid using emails for sharing sensitive information.
With this in mind, you need to develop the habit of checking the links that you click and the websites that you visit. Especially, if you’re on an office computer, exercise extra caution as criminals would send clocked baits to you. In addition, they would trick you with spear phishing and social engineering attacks as well.
To businesses, we’d suggest retraining your employees on phishing. Conduct the training with an emphasis on recent phishing examples, how to identify them, and how to report a suspicious email.
In our opinion, phishing training should be conducted regularly. This is because cybercriminals have been changing their tactics repeatedly. During the first few months of the pandemic, they used fake coronavirus tracking websites. Later, they shifted to COVID testing, the stimulus program, and the vaccines. Similarly, we might experience a spike in phishing attacks targeting the new relief aid as well.