HIPAA Compliance Definition
HIPAA Compliance refers to fulfilling the requirements of the Health Insurance Portability and Accountability Act (HIPAA) of 1996, a U.S. federal law designed to protect the privacy and security of patients’ medical information.
HIPAA Compliance History
The history of HIPAA (Health Insurance Portability and Accountability Act) compliance is rooted in the evolving needs of the healthcare system in the United States. Here’s a brief overview of its development:
- Early Foundations (Pre-1996): Before HIPAA was enacted, there was a growing concern about the security and privacy of personal health information, especially with the advent and rise of electronic medical records. Each state had its own laws regarding the privacy of medical information, which made it challenging for health systems operating in multiple states.
- The Birth of HIPAA (1996): The Health Insurance Portability and Accountability Act (HIPAA) was signed into law by President Bill Clinton on August 21, 1996. While it was initially focused on allowing persons to keep their health insurance between jobs (portability), it also aimed to make the healthcare system more efficient and to protect the privacy and security of patients’ health information.
- The Privacy Rule (2000-2003): The U.S. Department of Health and Human Services (HHS) published the final Privacy Rule in 2000, which set the first national standards for protecting the privacy of health information. After considering public feedback, HHS then published a final modified Privacy Rule in 2002, which became enforceable in 2003.
- The Security Rule (2003): After the Privacy Rule, the Security Rule was introduced in 2003. This rule set national standards for securing electronic protected health information (e-PHI).
- The Enforcement Rule (2006): This provided guidelines on investigations into compliance, as well as the imposition of civil money penalties for violations.
- HITECH Act (2009): The Health Information Technology for Economic and Clinical Health (HITECH) Act was enacted as part of the American Recovery and Reinvestment Act (ARRA) of 2009. The HITECH Act expanded upon the original HIPAA regulations. It introduced stricter enforcement and higher penalties for non-compliance and emphasized the importance of health information technology and electronic health records. The act also added provisions for breach notifications, requiring covered entities to inform affected individuals of unauthorized access to e-PHI.
- The Omnibus Rule (2013): This rule was an extensive update that implemented various provisions from the HITECH Act. It expanded the responsibilities of business associates, refined the definition of a breach, and increased the potential penalties for non-compliance.Table of Content
What Is Protected Health Information?
- Introduction
Protected Health Information, commonly referred to as PHI, is a term used within the U.S. healthcare sector to describe any information about health status, provision of healthcare, or payment for healthcare that can be linked to a specific individual. This is interpreted rather broadly and includes any part of a patient’s medical record or payment history. PHI is central to the Health Insurance Portability and Accountability Act (HIPAA) of 1996, which was enacted to protect patients’ health information from unauthorized access, use, or disclosure.
- Identifiers of PHI
HIPAA lists 18 specific identifiers that, when linked to health information, make it protected:
- Names: Full or last name, first initial.
- Geographic Data: Addresses smaller than the state level, including street address, city, county, or zip code.
- Dates: All except years that are directly related to the individual, including birthdate, admission date, discharge date, and date of death.
- Phone Numbers: Can be home, work, or mobile.
- Fax Numbers: Any fax numbers associated with the individual.
- Email Addresses: Any email addresses associated with the individual.
- Social Security Numbers: Entire number or part thereof.
- Medical Record Numbers: Any unique numbers or codes that hospitals or healthcare providers assign to patients.
- Health Plan Beneficiary Numbers: Numbers assigned by health insurers to individuals.
- Account Numbers: Any numbers associated with the individual’s account or payments.
- Certificate/License Numbers: Including driving licenses or professional certification numbers.
- Vehicle Identifiers and Serial Numbers: Including license plate numbers.
- Device Identifiers and Serial Numbers: IDs or serial numbers given to medical devices like pacemakers.
- URLs: Any URLs that can be traced back to the individual.
- IP Addresses: If it can be linked to an individual’s device or location.
- Biometric Identifiers: Fingerprints, voiceprints, retina scans, etc.
- Full Face Photos and Comparable Images: Including other identifying images.
- Any Other Unique Identifying Number, Characteristic, or Code: Anything else that can be used to trace back to an individual. Removing all these identifiers makes health information “de-identified,” and it’s no longer considered PHI under HIPAA. However, if there’s any chance that health information can be used alone or in combination with other data to identify an individual, it is considered PHI and is protected under HIPAA.
Who Needs to Be HIPAA-Compliant?
HIPAA compliance is required for certain entities and individuals who handle protected health information (PHI). Here are the primary groups that need to be HIPAA-compliant:
Covered Entities (CEs): This category encompasses:
Healthcare Providers: This includes doctors, clinics, psychologists, dentists, chiropractors, nursing homes, and pharmacies. However, they only need to be HIPAA-compliant if they transmit any information in an electronic form in connection with a transaction for which HHS has adopted a standard (e.g., electronic billing).
Health Plans: Including health insurance companies, HMOs (Health Maintenance Organizations), company health plans, and government programs that pay for healthcare such as Medicare, Medicaid, and the military and veterans’ healthcare programs.
Healthcare Clearinghouses: Entities that process nonstandard health information they receive from another entity into a standard format or vice versa.
Business Associates (BAs): These are third-party contractors that perform services for a covered entity and come into contact with, or handle, PHI in the process. This includes a broad range of entities such as:
- IT providers and consultants
- Billing and coding services
- Answering services
- Legal, actuarial, accounting, and consulting services
- Data processing firms or software companies that may access PHI
- Third-party administrators that help with the processing of health claims
- Certain researchers
- And many others.
Under the HIPAA Omnibus Rule of 2013, business associates are directly liable for compliance with specific requirements of HIPAA.
Subcontractors: These are entities or individuals hired by business associates. If they handle or have access to PHI on behalf of the business associate, they too are directly liable for HIPAA compliance.
Workforce Members of Covered Entities and Business Associates: This includes employees, volunteers, trainees, and others under the control of these entities, whether or not they are paid by them. They need to be trained and follow the HIPAA policies and procedures of the entity they work for.
Organized Health Care Arrangements (OHCA): When covered entities participate in joint activities and present themselves to the public as a single entity, they can share PHI among themselves for the joint healthcare activities without it being considered a violation.
[Also Read: Understanding HIPAA Privacy Rule: The Three Fundamental Rules to Keep in Mind]HIPAA Privacy and Security Rules
Introduction
The Health Insurance Portability and Accountability Act (HIPAA) is a crucial regulation in the U.S. healthcare system that ensures the protection of individuals’ health information. Two of its primary components are the Privacy Rule and the Security Rule, which provide standards for the protection of individuals’ medical records and other personal health information. Together, these rules establish a robust framework for maintaining the privacy and security of sensitive health data in various healthcare scenarios.
HIPAA Privacy
The HIPAA Privacy Rule, established in 2003, is designed to ensure the protection of individuals’ medical records and other personal health information maintained by covered entities, including healthcare providers, health plans, and healthcare clearinghouses. The rule:
- Right to Access: Grants individuals the right to access and obtain copies of their health information and to request corrections if they identify errors.
- Limits on Use: Limits how personal health information can be used and disclosed, allowing use only for patient care and other essential purposes.
- Minimum Necessary: Covered entities are required to disclose only the “minimum necessary” information to accomplish a task.
HIPAA Security
Introduced in 2005, the HIPAA Security Rule complements the Privacy Rule and sets standards for securing health information that is stored or transferred electronically (ePHI). The rule:
- Administrative Safeguards: Requires covered entities to conduct risk assessments and implement security policies, among other measures.
- Physical Safeguards: Details physical measures, policies, and procedures to protect electronic information systems and related buildings and equipment from natural and environmental hazards.
- Technical Safeguards: Requires controls like encryption, access controls, and audit controls to ensure only authorized individuals can access ePHI.
HIPAA Compliance Analysis
Ensuring HIPAA compliance requires covered entities to analyze their operations continuously. They must assess potential vulnerabilities in their PHI protection measures and rectify any identified gaps. This involves periodic risk assessments, employee training, policy updates, and ensuring that any third-party vendors or business associates are also compliant.
The Seven Elements of Effective Compliance
For a comprehensive and effective HIPAA compliance program, organizations can refer to these seven core elements:
1. Policies and Procedures: Develop and implement written policies, procedures, and standards of conduct.
2. Designated Compliance Officer: Appoint a compliance officer and compliance committee responsible for executing the program.
3. Training and Education: Conduct regular training and education for all employees and stakeholders.
4. Open Lines of Communication: Ensure a secure and anonymous means for individuals to report issues or ask questions.
5. Auditing and Monitoring: Conduct regular audits to assess performance and compliance, making necessary adjustments.
6. Enforcement Through Publicized Disciplinary Guidelines: Establish clear consequences for non-compliance, ensuring everyone is aware of them.
7Prompt Response to Detected Offenses and Corrective Action: Act swiftly when issues are identified, ensuring that corrective measures are implemented to prevent future occurrences.
Physical and Technical Safeguards, Policies, and HIPAA Compliance
The Health Insurance Portability and Accountability Act (HIPAA) has long stood as a pillar in the healthcare sector, ensuring that patients’ personal health information remains private and secure. While the act covers a broad scope, one of its critical components pertains to the safeguards and policies that organizations must implement. Here’s a brief dive into the essential facets of physical and technical safeguards, as well as policies and procedures under HIPAA.
- Physical Safeguard
Physical safeguards are the measures, policies, and procedures that protect electronic information systems, related equipment, and the buildings housing them from natural and environmental hazards and unauthorized intrusion.
- Facility Access Controls: These controls ensure that only authorized personnel can physically access buildings or areas housing e-PHI. This could include security guards, locked doors, or surveillance cameras.
- Workstation Use and Security: Organizations must specify what functions can be performed on specific workstations and ensure these stations are secure. For example, a computer with access to e-PHI might be positioned such that screen contents are not visible to casual passersby.
- Device and Media Controls: Policies should dictate how electronic media (e.g., USB drives, DVDs) containing e-PHI are removed, transferred, and disposed of. This ensures that unauthorized individuals cannot gain access to the data.
- Technical Safeguards
Technical safeguards involve the technology and its policies that protect e-PHI and control access to it.
- Access Control: This ensures only authorized personnel can access e-PHI. Implementations might include unique user IDs, an emergency access procedure, automatic logoff, and encryption.
- Audit Controls: Tracking logs and relevant activities in systems that contain or use e-PHI help ensure that data isn’t being accessed improperly.
- Integrity Controls: These controls ensure that e-PHI isn’t altered or destroyed without authorization. Mechanisms can be put in place to authenticate e-PHI to ensure data integrity.
- Transmission Security: When transmitting e-PHI, it must be protected against unauthorized access. This can be achieved using encryption, ensuring that data intercepted during transmission can’t be easily deciphered.
- Policy and Procedure
While having safeguards is critical, they are effective only if there’s a structured system guiding their implementation and maintenance. That’s where policies and procedures come into play.
- Regular Reviews: Organizations should periodically review and update their policies in light of environmental or operational changes affecting the security of e-PHI.
- Employee Training: All staff members must be aware of the organization’s policies and procedures. Regular training ensures that everyone knows their role in safeguarding e-PHI.
- Contingency Plans: In case of emergencies like fires, vandalism, or natural disasters, there must be explicit plans for data backup, disaster recovery, and emergency mode operation.
HIPAA Compliance Requirements
To be HIPAA compliant, organizations must not only implement these safeguards but also document them, regularly review and update them, and ensure that all staff members are aware and trained. Failing to comply can lead to significant penalties, both monetary and reputational. More than that, HIPAA compliance exemplifies an organization’s commitment to the privacy and security of the individuals they serve.
In a world increasingly reliant on digital data, it’s more important than ever for healthcare organizations to prioritize the protection of their patients’ sensitive information. Through robust physical and technical safeguards, underpinned by clear policies and procedures, HIPAA compliance ensures a framework for that protection.
HIPAA Compliance Violations
The Health Insurance Portability and Accountability Act (HIPAA) plays a vital role in the protection of patient health information. While many healthcare providers, health plans, and other entities work diligently to ensure compliance, violations still occur. Here’s an overview of HIPAA compliance violations:
- What are HIPAA Compliance Violations?
HIPAA compliance violations refer to breaches or non-compliance with the standards and provisions set by HIPAA regarding the protection, use, and disclosure of protected health information (PHI). These violations can occur when PHI is not adequately protected or is disclosed without appropriate authorization, either unintentionally or willfully.
- Types of Violations
Violations can vary in nature and severity. Here are some common types:
- Unintentional Violations: Often caused by lack of awareness, oversight, or accidents. Examples include misdirected emails, unsecured records, or loss of electronic devices containing PHI.
- Willful Neglect but Corrected: This pertains to organizations that have willfully ignored HIPAA requirements but have taken corrective actions within a specific timeframe.
- Willful Neglect and Not Corrected: When an entity consciously neglects HIPAA guidelines and makes no effort to correct them, severe penalties usually apply.
- Criminal Violations: These are intentional breaches for personal gain, harm, or malicious intent. Examples include selling PHI or accessing PHI without authorization for personal reasons.
- Penalties for Violations
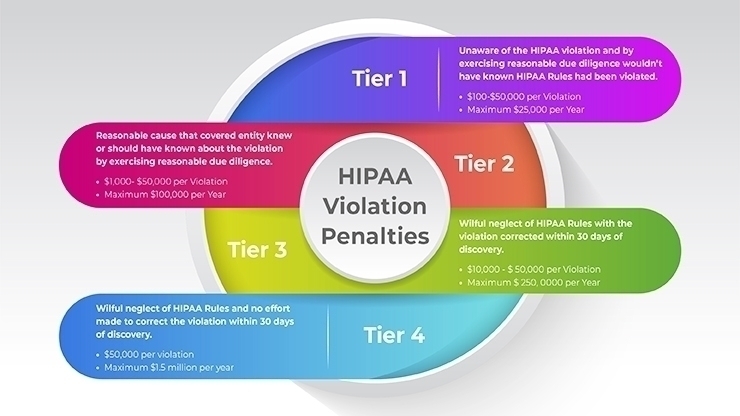
The penalties for HIPAA violations can be substantial, both in terms of monetary fines and criminal charges, and are tiered based on the perceived level of negligence:
- Tier 1: Unaware of the violation, and it couldn’t have been avoided with reasonable diligence. Fines range from $100 to $50,000 per violation.
- Tier 2: Violation due to reasonable cause and not willful neglect. Fines range from $1,000 to $50,000 per violation.
- Tier 3: Violation due to willful neglect, but corrective action was taken. Fines range from $10,000 to $50,000 per violation.
- Tier 4: Violation due to willful neglect and no corrective action taken. A fine of $50,000 per violation, with an annual maximum of $1.5 million for repeated violationsApart from monetary fines, criminal penalties can also apply, ranging from fines to imprisonment for up to 10 years, depending on the nature of the violation.
- Real-world Example
One of the most notable HIPAA violations involved the healthcare provider Anthem Inc. In 2015, Anthem experienced a cyberattack that led to the unauthorized exposure of nearly 79 million people’s PHI. This breach was attributed to inadequate measures in place to protect PHI. In 2018, Anthem agreed to pay the U.S. Department of Health and Human Services (HHS) $16 million, marking the largest U.S. settlement for a reported HIPAA violation.
Recent HIPAA Updates
in January 2022, there have been several notable updates to HIPAA regulations and guidance in the preceding years. It’s essential to keep in mind that regulations and guidance can evolve over time, and the U.S. Department of Health and Human Services (HHS) may have issued further updates after January 2022. That said, up to my last update, here are some recent key changes and updates related to HIPAA:
- HIPAA and COVID-19:
In response to the COVID-19 pandemic, the HHS issued several notifications of enforcement discretion and guidance to assist the healthcare industry in understanding how to navigate patient privacy and public health concerns:
- Telehealth Remote Communications: HHS announced it would not penalize providers for non-compliance with the regulatory requirements under the HIPAA Rules in connection with the good faith provision of telehealth services during the pandemic. This allowed more flexibility for providers to communicate with patients through everyday platforms.
- Community-Based Testing Sites: HHS announced they would not impose penalties for non-compliance with HIPAA on covered healthcare providers or their business associates in connection with the good faith participation in the operation of a COVID-19 community-based testing site during the nationwide public health emergency.
- Information Blocking and the Cures Act:
While not a direct HIPAA amendment, the 21st Century Cures Act introduced the “information blocking” rule. This rule promotes interoperability in healthcare and stipulates that patients should have access to their electronic health records without any deliberate delays or “blocking” by providers, developers of certified health IT, and health information networks/exchanges. - Amendments Related to Coordinated Care:
The HHS had proposed modifications to the HIPAA Privacy Rule to support coordinated care, aiming to promote value-based healthcare by examining and improving care coordination and case management. The proposed changes encompass:
- Reducing delays in care coordination.
Adjusting requirements on how individuals can access and obtain a copy of their health records.Introducing exceptions to the “minimum necessary” standard for data sharing for care coordination and case management.
How emPower eLearning solution Can Help
How emPower eLearning Solution Can Help with HIPAA Training and Compliance:
- Comprehensive Training Modules: eLearning platforms typically offer a range of training modules on various topics. For HIPAA, emPower can provide comprehensive training covering all aspects of the regulations, from privacy rules to security protocols.
- Interactive Learning: Through videos, quizzes, and interactive scenarios, users can engage with the content more effectively. This interactivity can enhance understanding and retention.
- Regular Updates: eLearning solutions often allow for easy content updates. As HIPAA regulations evolve, emPower can swiftly update training materials to reflect the latest changes, ensuring that learners are always receiving up-to-date information.
- Tracking and Reporting: Administrators can monitor the progress of individual learners, check quiz scores, and see who has completed the training. This feature is essential for ensuring compliance across an organization.
- Certification: Upon completing a training module, users might receive a certificate, verifying their understanding of HIPAA regulations. This can be beneficial for both employee records and organizational compliance documentation.
- Scalability: eLearning solutions like emPower can be scaled to accommodate organizations of all sizes. Whether you’re training a team of 10 or 10,000, the platform can handle it.
- Flexibility: Being an online platform, employees can access emPower anytime and anywhere. This flexibility means that training can fit into diverse schedules, making it easier for everyone to complete their HIPAA training.
- Customization: If emPower offers customizable content, organizations can tailor the training modules to address specific scenarios relevant to their operations.
- Cost-Efficient: eLearning often proves more cost-effective than traditional in-person training sessions, especially for large organizations. There’s no need for physical materials, venue rentals, or external trainers.
- Consistent Training: Everyone gets the same high-quality training. Unlike in-person sessions, where the trainer’s effectiveness might vary, eLearning ensures a consistent experience for all learners
- Community and Support: Some eLearning platforms offer forums or community support. If emPower has this feature, users can discuss topics, ask questions, and share insights with peers, enhancing the learning experience. In summary, if the emPower eLearning solution incorporates the typical features of advanced eLearning platforms, it can play a crucial role in disseminating essential HIPAA knowledge, ensuring compliance, and fostering a culture of data privacy and security within an organization.